15 managing disk - understanding encrypted LUKS partitions / dmsetup status / swapon -s
1. on device level you use fdisk to create a partition
2. once you created a partition, you use cryptsetup luksFormat\ to create encryption layer
3. after creation of encryption layer, you need to open a device cryptsetup luksOpen\
3.1. it creates a devices /dev/mapper/secret and brings to luks level
4. mkfs should be done on /dev/mapper/secretedevicename instead of on /dev/sdb1
5. mount /dev/mapper/secret and put your files there
check if there are any encrypted LUKS partitions
[root@svn ~]# blkid
/dev/sda1: UUID="6e3708b2-09ea-43f3-b0f0-9b43a157b3b1" TYPE="xfs"
/dev/sda2: UUID="98h644-2gqM-2SsL-q0lA-qUEE-Ivz8-TUZULc" TYPE="LVM2_member"
/dev/sdb1: LABEL="myfs" UUID="05dbcff3-e639-40cb-bbe7-0da595186f1a" TYPE="xfs"
/dev/sr0: UUID="2016-12-05-13-52-39-00" LABEL="CentOS 7 x86_64" TYPE="iso9660" PTTYPE="dos"
/dev/mapper/cl-root: UUID="da05cdf9-1418-4e5a-80d7-7757ab1b9a9d" TYPE="xfs"
/dev/mapper/cl-swap: UUID="8ac067b9-d1e7-4180-9a2f-2a3a929362f4" TYPE="swap"
[root@svn ~]# dmsetup status
cl-swap: 0 4194304 linear
cl-root: 0 35643392 linear
--------------
ubuntu-home: 0 195305472 linear
ubuntu-swap_1: 0 8364032 linear
sda5_crypt: 0 624637944 crypt
ubuntu-root: 0 48824320 linear
The line marked "crypt" shows that sda5 has been encrypted. You can see which filesystems are on that via the lvm tools.
#check real device name of swap
[root@svn ~]# swapon -s
Filename Type Size Used Priority
/dev/dm-1 partition 2097148 3124 -1
[root@svn ~]#
If the partition is not encrypted, and assuming that you are NOT trying to encrypt the
/ partition, you have to:- Make a backup of the data on that partition
- Initialize the partition as encrypted
$ cryptsetup luksFormat /dev/sdb1
BEWARE: this command will wipe all the contents of the partition!!! It will ask you for a passphrase to open the volume; now if you try to run
blkid, the output should be TYPE="crypto_LUKS"- Open the encrypted partition to use it
$ cryptsetup luksOpen /dev/sdb1 secret
where "
secret" is the name of the volume we are opening- Format the new "
secret" volume$ mkfs.ext4 /dev/mapper/secret - Mount it providing the passphrase created before
$ mount /dev/mapper/secret /whereyouwantNow you should be able to use the encrypted partition!
Optionally, if you want to mount it at reboot, you should edit
/etc/crypttab and insert a line similar to this (it will request the password at boot):secret /dev/sdb1 none
Where
secret is the name of the volume we created before.
Or something like this, if you want to put your password in some plain text file:
secret /dev/sdb1 /whereyouwant-sdb1-luks-pwdfile
Just keep in mind for this, you also have to add the key:
$ cryptsetup luksAddKey /dev/sdb1 /whereyouwant-sdb1-luks-pwdfile
And edit the
/etc/fstab and insert a line similar to this:/dev/mapper/secret /whereyouwant ext4 defaults 1 2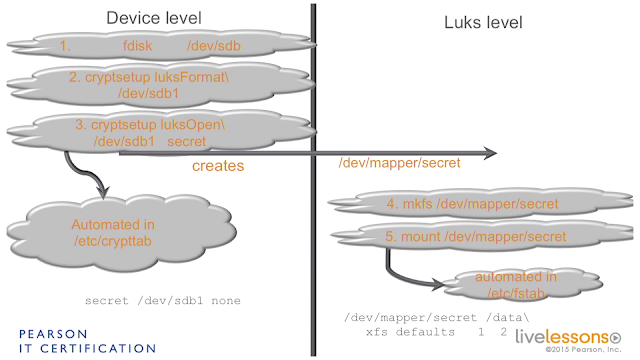
Comments
Post a Comment